Learn to Navigate Cyber Threats this Cybersecurity Awareness Month
Introduction
Technology is evolving to enhance our experience with so many tools and services online. In the meantime, cyber criminals are finding news ways to steal precious information and personal funds. Want to stay safe online? Check out our 2024 Cybersecurity Awareness Student Campaign: Navigating Cyber Threats
You wouldn’t leave your home without checking the weather forecast—so why go online without being prepared? Like storm clouds, cyber scams can appear out of nowhere and disrupt your day.
Learn to navigate through potential scams and protect yourself from phishing attempts, malware, and other cyber threats to keep your information, data, and devices secure.
Forecasting Scams: Recognize Phishing Attempts

“Phishing” is a form of cybercrime where attackers pose as legitimate entities to deceive individuals into giving up sensitive information such as passwords, credit card numbers, or social security numbers. These attacks often come through emails or text messages that appear authentic, making it challenging for unsuspecting recipients to identify the threat. Beware of scam emails with the following typical “features”:
Appear Legitimate
Phishing scam emails can seem legitimate and appear to come from a known contact, a well-known organization, or a program that you use every day at school or work. Scammers often use hacked accounts or look-alike imposter accounts to trick you. Phishing emails can even appear to come from an @uic.eud email address!
Contain Links
Phishing emails contain links that redirect to cleverly designed but fake websites where you’re prompted to enter sensitive information, such as logins and passwords.
Provide Alternate Email
To avoid detection, bypass security measures, and increase their control, phishing emails often instruct recipients to reply to a different email address or via SMS, or to use your personal email address.
Use Generic or Urgent Language
These emails will use generic greetings like “Dear Sir,” convey a sense of urgency or threat, and typically have grammatical errors and typos.
Secure Your Data: Use Strong Passwords
With cybercrime on the rise, password management – the practice of creating, storing, and managing passwords in a secure manner – is crucial for maintaining online security more than ever. Strong password practices protect against unauthorized access to personal and sensitive information.
For students, who often juggle multiple accounts for educational and personal use, robust password management is essential to stay safe online. Keep your data secure by:
Creating Strong, Unique Passwords
- Use uppercase and lowercase letters, numbers, and special characters.
- Ensure each account has a distinct password to prevent a single breach from compromising multiple accounts.
Using Password Managers
- Password managers are tools that store and manage your passwords, notes, and other sensitive data in an encrypted format.
Enabling Two-Factor Authentication (2FA)
- 2FA adds an extra layer of security by requiring a second form of verification, such as a code sent to your phone or an authentication app. This significantly reduces the risk of unauthorized access.
- Many online services and educational platforms support 2FA, making it a readily available option for students. UIC uses Duo 2FA.
Avoid Foggy Systems: Keep Software Updated & Uninstall Unused Software

Having out-of-date and unused software on your system can use resources to keep your system in the fog and running slowly. Uninstall software you’re no longer using to ensure your system has the resources to keep running smoothly.
Keeping software updated is crucial for maintaining the security and functionality of computers and mobile devices. For students, who rely heavily on technology daily, regular software updates are even more essential. Avoid foggy systems, here are three reasons why you should prioritize updating your software:
Enhanced Security
Outdated software is a prime target for cybercriminals. Software updates often include patches for security vulnerabilities that hackers can exploit. By keeping your software current, you significantly reduce the risk of malware infections, data breaches, and other cyber threats. Students are particularly vulnerable as they frequently use public Wi-Fi networks and access various online resources, making robust security measures essential.
Improved Performance and Stability
Software updates not only address security issues but also fix bugs and improve overall performance. Updated software runs more efficiently, with fewer crashes and glitches. For students, this means a smoother experience when working on assignments, conducting research, or participating in online classes. By ensuring their devices run optimally, students can avoid frustrating disruptions and maintain their productivity.
Access to New Features
Developers continually enhance software with new features and functionalities. These updates can include tools and improvements that make tasks easier and more enjoyable. For students, staying updated means having access to the latest educational tools, better compatibility with new applications, and enhanced user experiences. Embracing these updates can provide a competitive edge in their academic and personal endeavors.
Protect Your Information: Practice Safe Browsing

In today’s digital age, browsing the internet safely is crucial to protect personal information and avoid cyber threats. While the internet offers vast resources and conveniences, it also harbors risks such as malware and deceptive deep fake websites. Here are some essential safe-browsing tips:
Practice General Safe Browsing Habits:
- Be Cautious with Personal Information: Avoid sharing excessive personal details online, especially on social media, which can be used for identity theft.
- Avoid Suspicious Downloads: Download software and files only from trusted sources. Be wary of free software from unknown websites, which may contain malware.
- Use Reliable Antivirus Software: Ensure you have reputable antivirus software installed and keep it updated to detect and remove malware.
Identify and Avoid Deep Fake Websites:
- Check URLs Carefully: Deep fake websites often mimic legitimate sites with slight variations in their URLs. Always verify the web address before entering any sensitive information.
- Look for Security Indicators: Ensure the website uses HTTPS (look for a padlock icon in the address bar), indicating a secure connection.
- Use Trusted Links: Navigate to websites through trusted bookmarks or official search engine results rather than clicking on links in emails or social media.
Stay Updated on the Latest in Cybersecurity:
- Stay informed about the latest online threats and safe browsing practices. Regularly review privacy settings on your online accounts.
Keep Your Cybersecurity Forecast Clear: Know How to Get Support
Knowing when and how to get support is crucial to cybersecurity. If you think you’ve been a victim of a phishing attempt, contact support and know how to get assistance to keep your cybersecurity forecast clear.
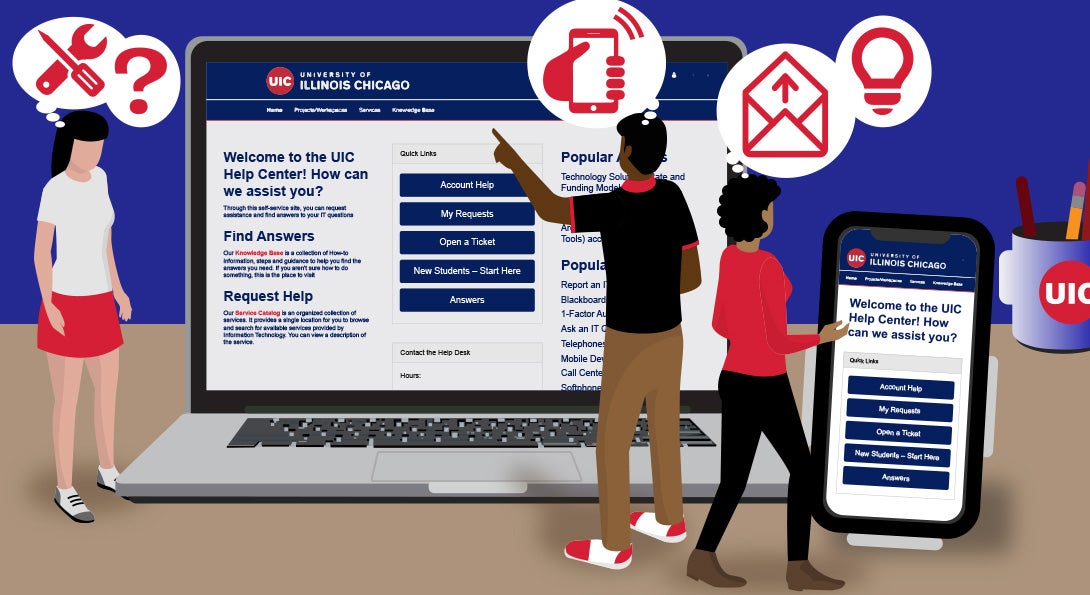
Get support at the UIC Help Center (help.uic.edu).
Visit the UIC Help Center to get support, reset your password, and find answers to frequently asked technology support questions.
Report suspicious emails to security@uic.edu.
The UIC Information Security team is dedicated to keeping the UIC Community safe from existing and potential security threats. Report and share suspicious emails to security@uic.edu for review and evaluation.
Take the Student Cybersecurity Awareness Quiz
Test your knowledge and enter for your chance to win a $50 gift card to UIC Bookstore! Students scoring 100% will be entered in a random drawing. You may take the quiz as many times as you would like to score 100%, however, your submission to the random drawing will count once.
By submitting a quiz, you agree to the 2024 Cyberseurity Quiz Rules.